In 2018, one of the most notable hotel chains worldwide experienced a massive data breach, leaving a trail of monetary damage, compromised trust, and a tarnished reputation—a shadow from which they are still trying to escape.
While security breaches aren’t new, this particular incident sent shockwaves throughout the hospitality industry, causing many hoteliers to take a step back and evaluate the security of their software.
After all, they don’t just have to protect guest data from being exploited, but they also have to safeguard their operational and accounting information.
And if you haven’t considered assessing your software’s security, we’re here to give you three you should start.
| Key Takeaways |
|
Reason 1: Emerging Technologies Pose New Threats
While it might seem like the hospitality industry has remained relatively unscathed when it comes to cyber attacks, the truth is that there are a string of security breaches that stretch throughout the years.
In fact, the hospitality industry was one of the top five industries that cyber criminals focused their attacks on in 2021, falling behind banking, industrial, and consumer goods and services.
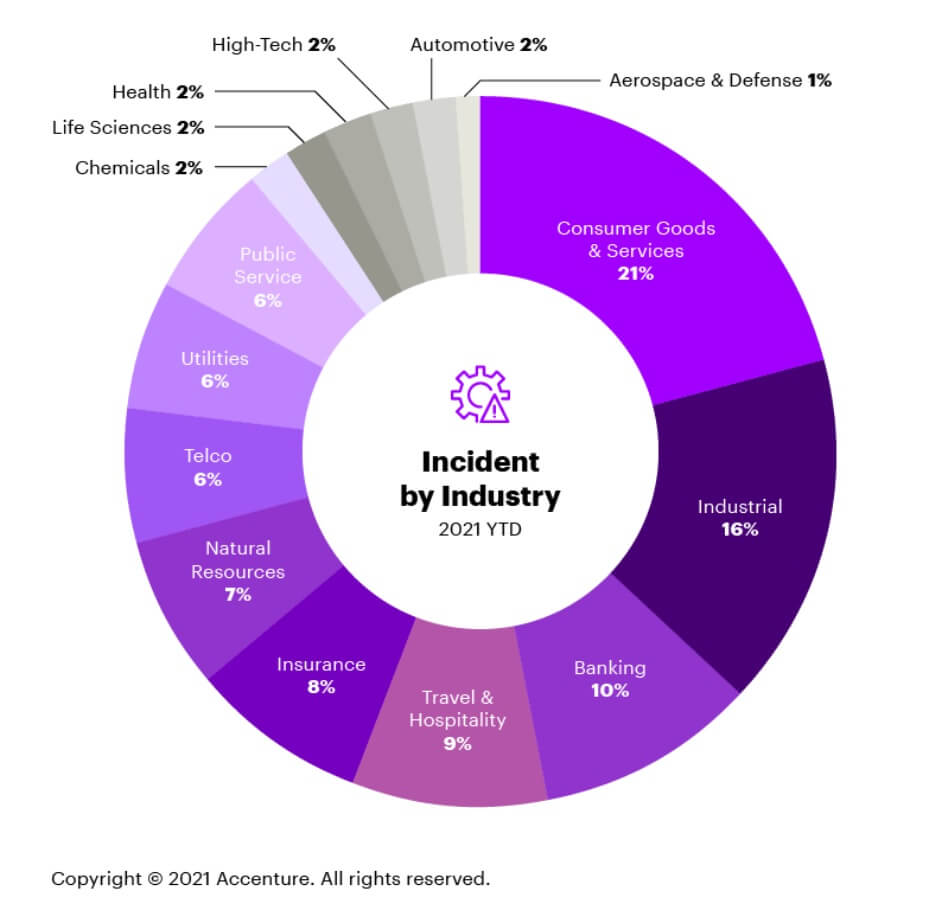
And with the emergence of artificial intelligence (AI) and machine learning, the threat of cyber-attacks has magnified.
Even though AI can be used to enhance a software’s security measures, in the wrong hands, it gives cybercriminals powerful tools to launch increasingly sophisticated attacks on hotel software.
These are just a few of the ways they are utilizing this technology to gain access to your software and the sensitive data it contains:
- Phishing attacks: While these aren’t new, they still remain one of the most effective types of attacks, and AI can now be harnessed to create convincing fake emails and websites that trick employees into revealing sensitive information or accessing sensitive financial information. On top of that, these attacks can now target individuals based on their online behavior and communication style, making them appear more legitimate.
- Deep fakes: AI can generate fabricated audio and video content, impersonating hotel staff or executives. Cybercriminals can use this to staff into disclosing sensitive information or carrying out actions that compromise security.
- Password cracking: With the help of AI, malicious actors can crack passwords at an unprecedented speed. They can analyze large data sets to predict password patterns, making it easier to gain unauthorized access to systems.
- Advanced Persistent Threats (APTs): These long-term targeted attacks use AI to blend in with normal network traffic so they can slowly siphon off sensitive data, making them incredibly hard to detect. They are one of the leading cyber threats to the hospitality industry.
- Automated malware: AI can enable malware to change its code automatically, helping it to avoid detection by security systems.
Reason 2: Legacy Systems Don’t Offer the Same Protection As Cloud-based Solutions
Although traditional legacy systems (non-cloud-based or on-premise solutions) functioned as the go-to for all back-office accounting business intelligence (BI) needs, they simply cannot meet the demands of today’s cyber attacks—even if they try to retrofit their software with some cloud capabilities.
Here’s why:
- They lack modern security protocols: Most legacy systems are built around security protocols that, while effective in the past, fall short of protecting against current, AI-fueled cyber attacks. This inability to keep pace with advanced threats leaves the systems and their data vulnerable to unauthorized access and breaches.
- They have limited remote access (if at all): With many hotel chains operating across various locations, remote access to the back office accounting and BI systems is crucial, but it’s not something legacy systems often support. This limitation impedes real-time monitoring and rapid response to potential threats, which can lead to unnoticed or unresolved breaches for extended durations.
- Patches and updates take too long: The process of updating security features on these systems is typically slow and intricate. This delay gives cyber-criminals a time window to exploit system vulnerabilities before they are rectified.
- The risk of data loss is much higher: From accidentally deleted data or system failures to physical catastrophes, data on traditional, non-cloud-based systems risk being permanently lost if not properly backed up. Loss of crucial financial and performance data has the potential to cripple a hotel’s strategic operations.
- They don’t integrate well with modern applications and lack secure data exchanges: As hotel operations rely increasingly on modern applications, legacy systems struggle with seamless, secure integration, resulting in operational gaps and data inaccuracies. These systems also lack advanced encryptions and secure APIs to transfer data between systems, leaving data exposed to cyber threats.
Reason 3: It’s Going to Cost You
From guest profiles and credit card information to internal operational metrics, hotels are a goldmine of data. The complexity and value of these data streams make hotels a prime target for cyber attacks.
On top of that, pandemic-facilitated contactless and mobile services and other third-party integrations present additional vulnerabilities that can be exploited if not properly protected.
Failing to prioritize security in these circumstances could lead to disastrous and very costly consequences. In fact, the average cost of a data breach cost an average of $4.24 million.
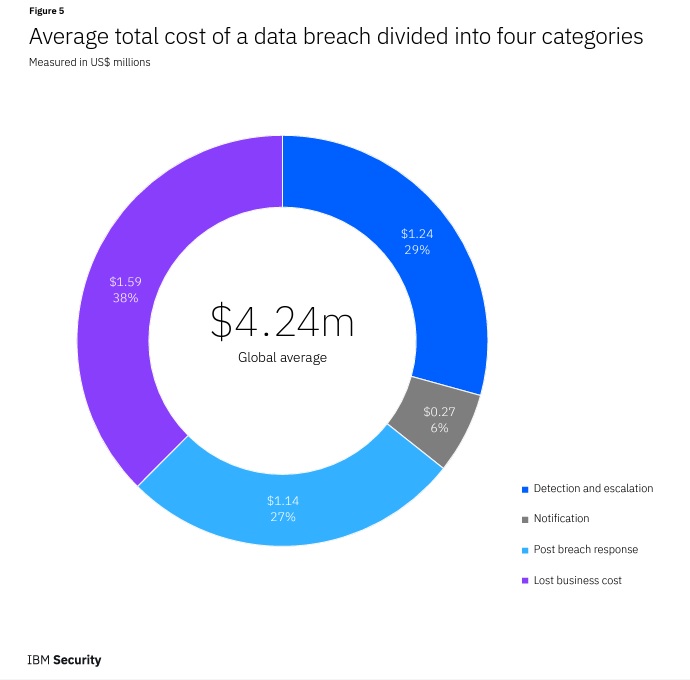
Here are just a few of the other impacts you’ll see if you experience a data breach:
- Stiff Financial Penalties: Over the years, new legislation, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), have been implemented to protect sensitive data. Failure to comply with these laws can attract enormous fines.
- Legal Action: On top of paying hefty fines, any breach due to inadequate security measures can result in lawsuits, further financial penalties, and irreparable damage to your hotel’s reputation.
- Loss of Customer Trust: Hotels are built on trust, and a breach can lead to an erosion of reputation among guests and can cause them to take their business elsewhere.
- Operational Disruption and Loss of Revenue: A significant breach can disrupt day-to-day operations and have lasting impacts, which could take years to recover from.
What Can You Do?
The first step in securing your hotel’s data is acknowledging the need for robust and modern cybersecurity measures—which typically requires opting for a true cloud-based software solution for your back office.
True Cloud-based systems:
- Are built from the ground up with state-of-the-art security protocols to address modern security challenges.
- Come equipped with multi-layer security protocols, including advanced encryption algorithms and feature frequent automated security updates and patches, providing a much higher level of protection compared to traditional legacy systems.
- Have the built-in capacity for real-time AI monitoring of system activities, allowing for the swift identification and mitigation of potential threats.
- Offer frequent data backup and recovery benefits that allow you to protect your information in the event of a physical disaster or system failure, preventing permanent data loss. For example, HIA software runs frequent multiple redundant backups because restoring even one day’s transactions can result in significant downtime.
- Are crafted to meet international data protection regulations like GDPR and CCPA, ensuring your hotel adheres to stringent data privacy standards.
- Provide secure access or APIs for third-party integrations so you can safely integrate them into your processes without compromising safety.
- Provide administrator control over role access. True-cloud software such as HIA enables full control over user privileges, such as what data they can access within the system from where they can log in – such as limiting by location or IP address – complexity requirements, frequency of password changes, multi-factor authentication, and more.
For on-premise solutions and/or solutions not built on the cloud, providing this level of complex security would be difficult and costly. While transitioning to a true cloud-based solution might sound like a straightforward solution, we understand that it’s not something everyone is capable of implementing immediately.
Migrating your systems can be a significant undertaking that requires careful planning, strategic investment, and the right partner. Just remember, the decision to switch to secure hotel software isn’t just an expense—it’s a strategic investment in your business’s longevity and reputation.
When you’re ready to take the next step towards a more secure and streamlined future, we at HIA are here to assist. We are committed to helping businesses like yours navigate this transition with minimal disruption to your operations.
If you want to learn more about our secure, cloud-based financial management and BI solutions, reach out to a member of our team.










